You've opened a suspicious email attachment and put your device at risk of compromise. Fortunately, this was only a test. Please take a few minutes to read this page so you can learn how to protect yourself against real attacks in the future.
Clicking a suspicious link isn't the only way scammers snag people with phishing emails—getting recipients to download infected or otherwise malicious email attachments is another common strategy. Had the email you received been an actual phish, opening the attachment could have infected your computer or device with a "drive-by download"—malicious software programs that are installed silently and attempt to steal your passwords and personal information, or even lock you out of your device (via "ransomware").
The email you received may have looked legitimate—and that's the point. As someone affiliated with engineering or natural sciences on campus, you're a prime target for advanced nation-state groups looking for entry points into UT's networks and research data. These groups often craft very legitimate-looking emails designed to engage you and gain your trust. But, there are a few clues that should lead you to think twice about the legitimacy of this email: its sender address, its unsolicited nature, its generic content, and its unusual attachment. Let's look at the specifics:
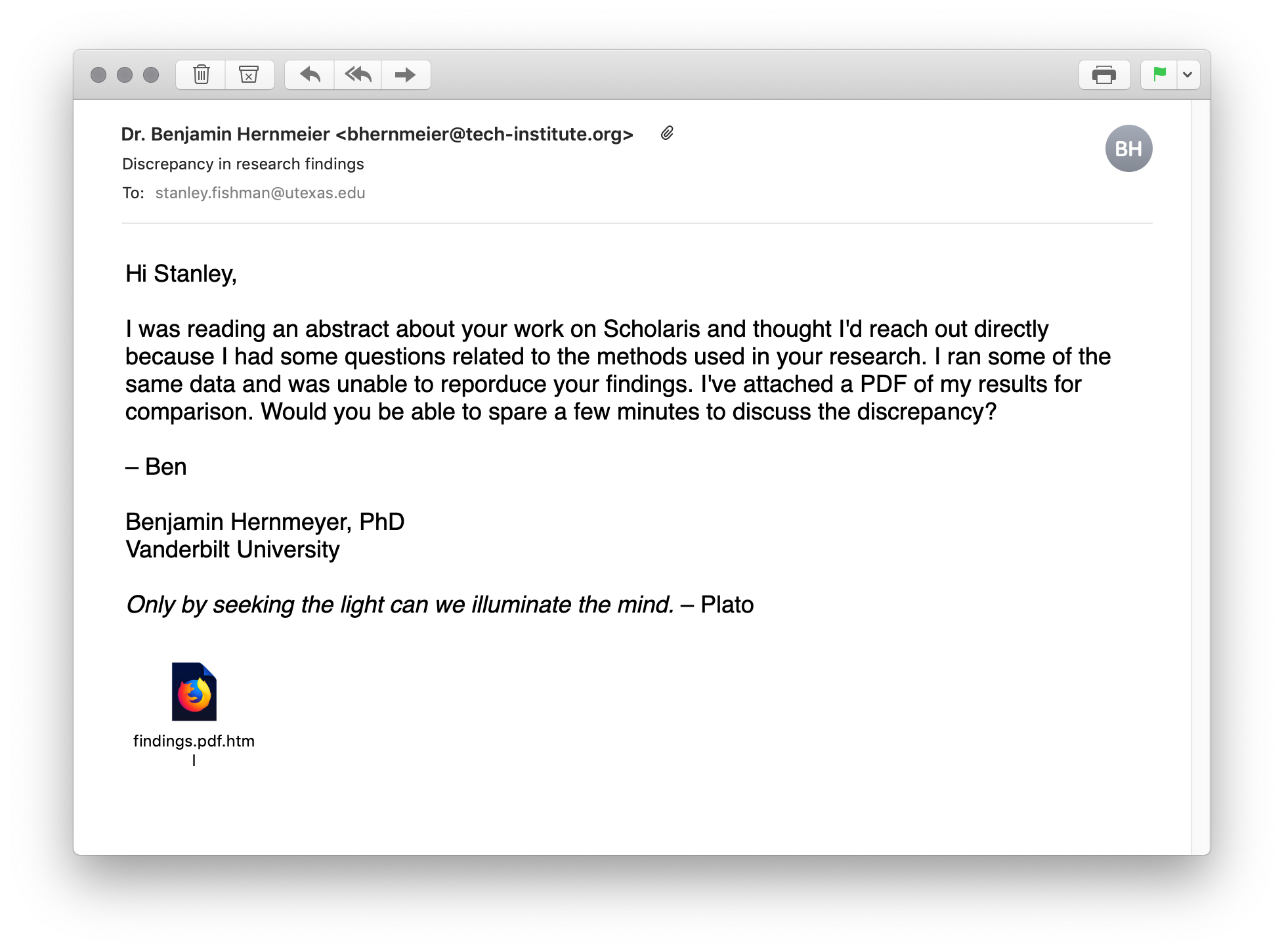
- The sender is using a plausible name but, if you look at the address, it's using the domain name "tech-institute.org". His email signature claims he is affiliated with Vanderbilt University; not using a vanderbilt.edu address should raise doubts.
- Were you expecting this email? Do you know who Benjamin Hernmeier is? Have you ever heard of Scholaris? A quick Google search would tell you that this is likely a fictitious name and a nonexistent service.
- Notice how the message tries to hook you by implying that your research was flawed? That drives a common reaction to want to defend yourself by replying, or at least by looking at the supposed evidence in the attachment. But, nowhere in this email does the sender mention any specifics of your actual research. Another red flag!
- Most importantly, unsolicited attachments should always be regarded with suspicion. These are one of the most common methods by which ransomware is spread. It's also suspicious that the sender claims he sent a PDF, while the actual attachment is an HTML file (findings.pdf.html). In any case, unsolicited email attachments should always be regarded as dangerous. If you receive an unexpected attachment, it's a good strategy to confirm that the purported sender actually sent the email; one way to do this would be to call the sender on the phone, or communicate with them via a chat service like Slack or Microsoft Teams.
These clues should cast doubt on the legitimacy of the email. Always check with your technical support contacts, the UT Service Desk, or the Information Security Office before clicking links in suspicious emails, providing information to suspicious websites, downloading unexpected attachments, or replying to suspicious messages. You can also forward suspected phishing messages to postmaster@utexas.edu.
