You've clicked on a suspicious email link and put your device at risk of compromise. Fortunately, this was only a test. Please take 5 minutes and read this page so you can protect yourself against real attacks in the future.
Phishing emails entice you with attractive offers, or scare you with threats of loss, to trick you into visiting a malicious site and, often, handing over sensitive information. Had the email you received been an actual phish, clicking the link could have infected your computer or device with a "drive-by download"—malicious software programs that are installed silently and attempt to steal your passwords, personal information, or even lock you out of your device.
If you suspect you've received a phishing email, forward it to postmaster@utexas.edu and notify your local IT staff. Never click on any links contained in the message, or reply to the sender.
Let’s learn how you can detect phishing attacks like these so you don’t get caught by a real attack in the future.
This email may have piqued your curiosity, especially because it bears a strong resemblance to order confirmation emails sent by a certain large online retailer. But, several clues should lead you to think twice about the legitimacy of this email: its sender address, its unexpected nature, its misspellings, and its suspicious hyperlinks. Let's look at the specifics:
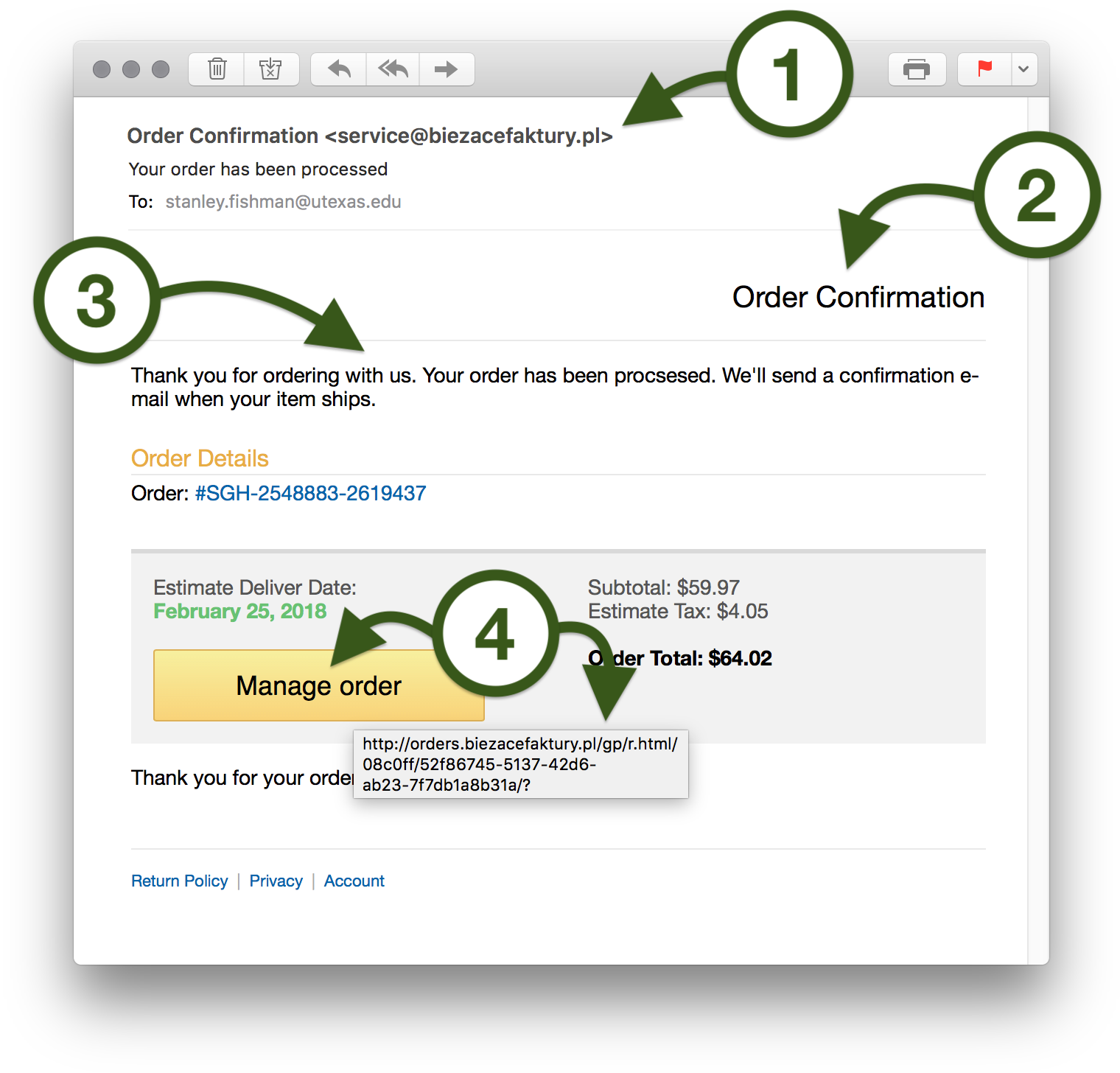
- The sender has set his display name to "Order Confirmation" but the sender's actual address shows its real origin: service@biezacefaktury.pl. This domain name is clearly not associated with UT Austin—or any recognizable online retailer—and should immediately raise doubts.
- Think about it: have you ordered anything recently using your UT Austin email address? If not, why are you receiving an order confirmation? This email doesn't even specify the retailer with which you placed the supposed order. In fact, it contains no identifying information about the business, at all. Would any legitimate business fail to mention its own name?
- The body of this message contains misspellings, like "procsesed" and "Estimate Deliver Date". It's unlikely that a professionally drafted message from a legitimate business would be written so carelessly.
- Hover over this hyperlink before clicking, and you'll see that it points to biezacefaktury.pl, an unknown website that is clearly not affiliated with any retailer with which you've done business. In fact, that website address means "current invoices" in Polish.
This email may have piqued your curiosity, especially because it bears a strong resemblance to order confirmation emails sent by a certain large online retailer. But, several clues should lead you to think twice about the legitimacy of this email: its sender address, its unexpected nature, its misspellings, and its suspicious hyperlinks. Let's look at the specifics:
- The sender has set his display name to "Order Confirmation" but the sender's actual address shows its real origin: service@biezacefaktury.pl. This domain name is clearly not associated with UT Austin—or any recognizable online retailer—and should immediately raise doubts. Note that, on mobile devices, you may need to tap the "Details" button to see the sender's actual email address.
- Think about it: have you ordered anything recently using your UT Austin email address? If not, why are you receiving an order confirmation? This email doesn't even specify the retailer with which you placed the supposed order. In fact, it contains no identifying information about the business, at all. Would any legitimate business fail to mention its own name?
- The body of this message contains misspellings, like "procsesed" and "Estimate Deliver Date". It's unlikely that a professionally drafted message from a legitimate business would be written so carelessly.
- Long-press (tap and hold for 1-2 seconds) on this hyperlink instead of tapping, and you'll see that it points to biezacefaktury.pl, an unknown website that is clearly not affiliated with any retailer with which you've done business. In fact, that website address means "current invoices" in Polish.
When you're inspecting a link, or on a website, how do you know it's legitimate or not?
Links have lots of information in them. They can be daunting. We'll break it down so you can focus on the most important part. Take this link, used in a real phishing attack.
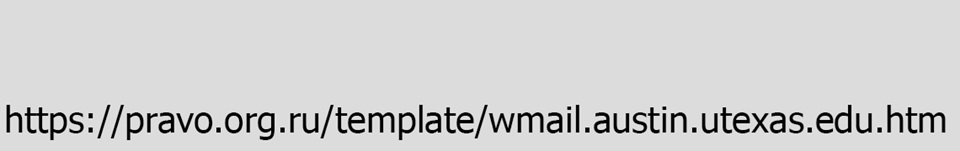
That's a lot of information, and some of it looks legitimate. But once you understand the structure of links, it becomes easy to see why this is a malicious link.
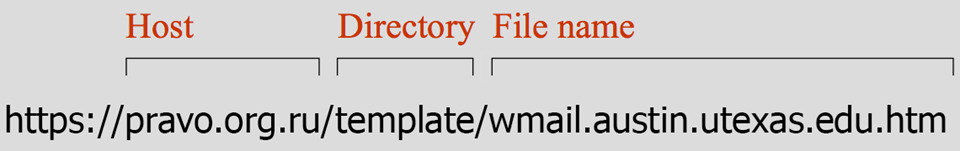
Websites are hosted on computers, much like the ones in your office. The Host part of a link tells you the name of the computer.
And just as your computer has files and folders on it, websites have them too. The Directory part of a link is just like a folder path on your computer. The very last piece of a link is the File name. It tells you the file you’re looking at, just like a Word document or spreadsheet on your computer.
So now we know what all this information means. What’s really important?
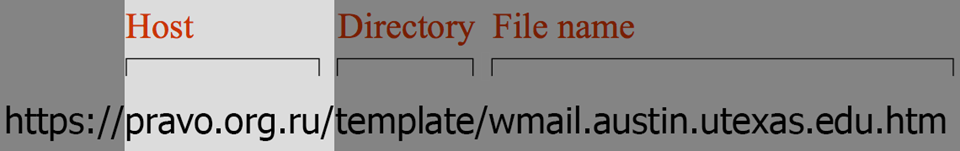
No matter how long and confusing a link is, the Host is all you need to focus on. Attackers can manipulate the Directory and File name to look like legitimate content, but they can never change their Host to perfectly match a legitimate one. Let’s look at a legitimate Host now.
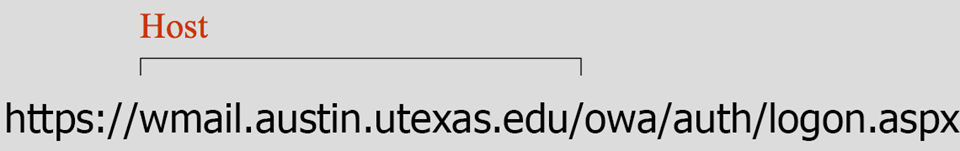
Now that we know the Host is what's really important, let's focus even more. Find the first single "/" in the link.
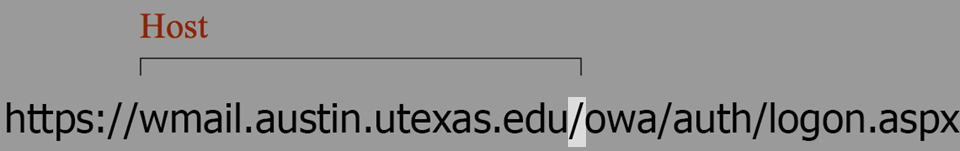
Look at the two words to the left of it, separated by a "." Those two words can never be manipulated; they always tell you a website’s true identity.
In the image below, those two words are "utexas" and "edu".
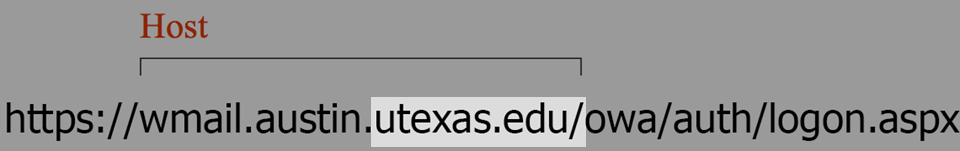

Compare the two images above. In the first, utexas.edu is the true source of the link, while the second one is org.ru. Look at the rest of the org.ru link. You can see its File name is trying to impersonate the Host of the first link!
Take a look at your web browser to find the address of the site you’re on, right now. What is its true source?
These clues should cast doubt on the legitimacy of the email. Always check with your technical support contacts, the UT Service Desk, or the Information Security Office before clicking links in suspicious emails, or providing information to suspicious websites.
