You've clicked on a suspicious email link and gave your password to an illegitimate website. Fortunately, this was only a test. Please take 5 minutes and read this page so you can protect yourself against real attacks in the future.
Phishing emails entice you with attractive offers, or scare you with threats of loss, to trick you into visiting a malicious site and, often, handing over sensitive information. Had the email you received been an actual phish, clicking the link could have infected your computer or device with a "drive-by download"—malicious software programs that are installed silently and attempt to steal your passwords, personal information, or even lock you out of your device. Giving your email address and password to an illegitimate website would have let hackers read your email, reset account passwords, and access lots of your personal information.
If you suspect you've received a phishing email, forward it to postmaster@utexas.edu and notify your local IT staff.
Let’s learn how you can detect phishing attacks like these so you don’t get caught by a real attack in the future.
This email may have seemed legitimate, especially because UT has an employee discount program called LifeMart. But, several clues should lead you to think twice about the legitimacy of this email: its sender address, its poor use of the English language, and its suspicious hyperlinks. Let's look at the hard evidence:
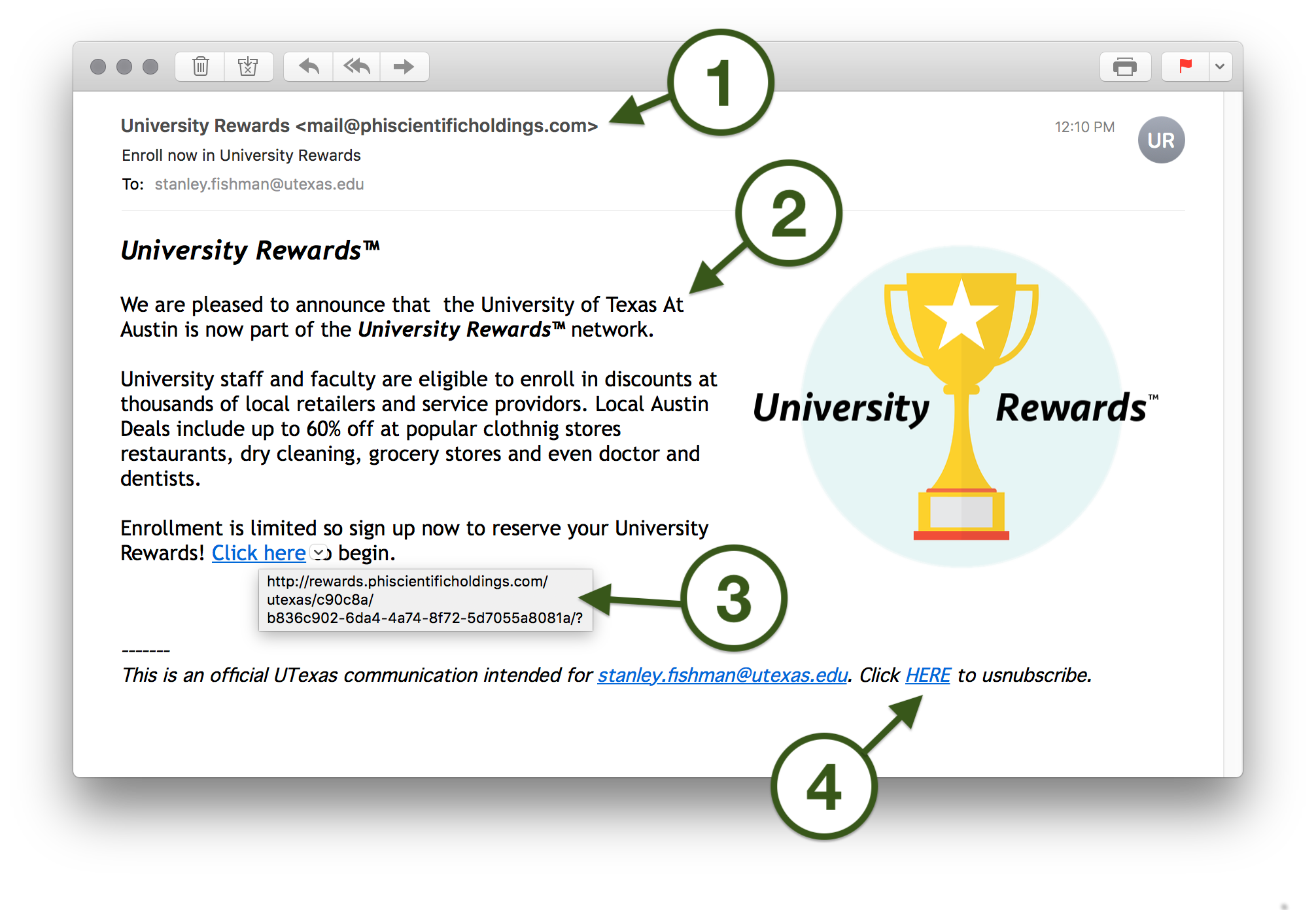
- The sender has set his display name to "University Rewards" but the sender's actual address shows its real origin: mail@phiscientificholdings.com. This domain name is clearly not associated with UT Austin and should immediately raise doubts.
- The body of this message contains numerous misspellings, poor grammar, and strange spacing. It's unlikely that a professionally drafted message from the University or one of its business partners would be written so carelessly.
- Hover over this hyperlink before clicking, and you'll see that it points to phiscientificholdings.com, an unknown website that is clearly not affiliated with UT Austin.
- This hyperlink, which is ostensibly to unsubscribe from future mailings, also points to the shady and unknown website phiscientificholdings.com. It is not an official University website, such as utexas.edu.
This email may have seemed legitimate, especially because UT has an employee discount program called LifeMart. But, several clues should lead you to think twice about the legitimacy of this email: its sender address, its poor use of the English language, and its suspicious hyperlinks. Let's look at the hard evidence:
- The sender has set his display name to "University Rewards" but the sender's actual address shows its real origin: mail@phiscientificholdings.com. This domain name is clearly not associated with UT Austin and should immediately raise doubts. Note that, on mobile devices, you may need to tap the "Details" button to see the sender's actual email address.
- The body of this message contains numerous misspellings, poor grammar, and strange spacing. It's unlikely that a professionally drafted message from the University or one of its business partners would be written so carelessly.
- Long-press (tap and hold for 1-2 seconds) on this hyperlink instead of tapping, and you'll see that it points to phiscientificholdings.com, an unknown website that is clearly not affiliated with UT Austin.
- This hyperlink, which is ostensibly to unsubscribe from future mailings, also points to the shady and unknown website phiscientificholdings.com. It is not an official University website, such as utexas.edu.
Even if you clicked on the email's suspicious hyperlinks, the webpage that comes up has several clues that should lead you to think twice about its legitimacy: its URL, its lack a security certificate, its poor use of the English language, and its suspicious hyperlinks. Let's look at the hard evidence:
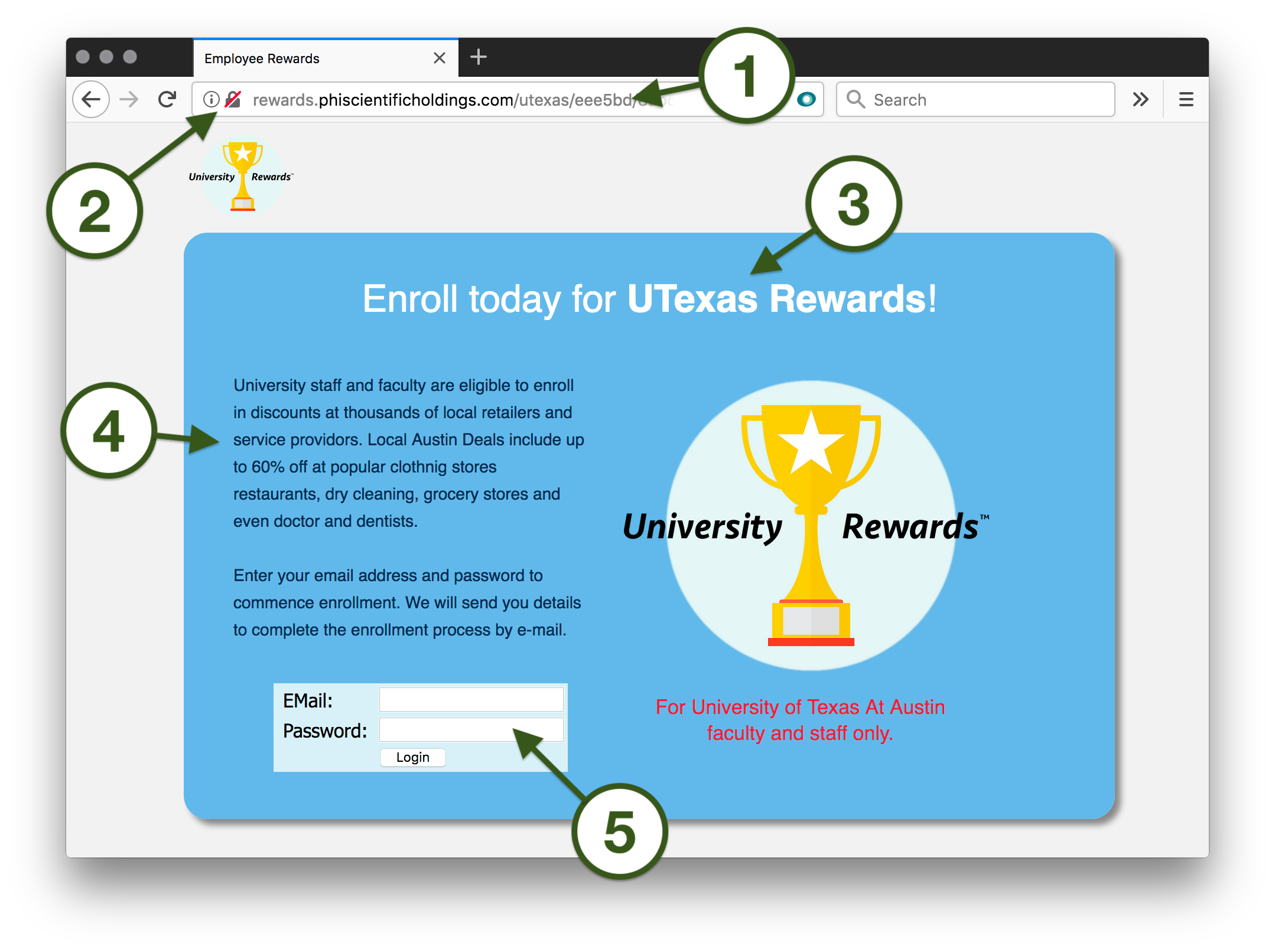
- Look closely at the URL of this webpage; the words before the first slash ( / ) are not "utexas.edu" but rather phiscientificholdings.com. This URL has no affiliation with the University and should be viewed as suspicious.
- All University websites that ask you to submit information will use a security feature called SSL/TLS, which ensures that information you transmit is sent securely. Your browser will show a green padlock for websites that provide this feature. In this case, the web browser shows a padlock with a red slash through it, showing that information sent to this website will not be sent securely. Never enter sensitive information on a website unless it uses SSL/TLS.
- The heading on this page isn't consistent—the program is supposedly called "University Rewards" but this page calls it both University Rewards and "UTexas Rewards". This shows a lack of attention to detail.
- The same misspellings, strange spacing, and poor grammar from the email also turn up on this webpage. Few professional websites would neglect even to use spell-check before publishing their content.
- Your web browser likely warns you that this submission form is not secure the moment you put your cursor in the box to begin typing. Heed your browser's warning and never submit your information to suspicious websites.
When you're inspecting a link, or on a website, how do you know it's legitimate or not?
Links have lots of information in them. They can be daunting. We'll break it down so you can focus on the most important part. Take this link, used in a real phishing attack.
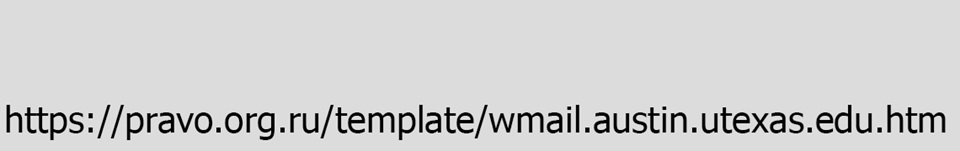
That's a lot of information, and some of it looks legitimate. But once you understand the structure of links, it becomes easy to see why this is a malicious link.
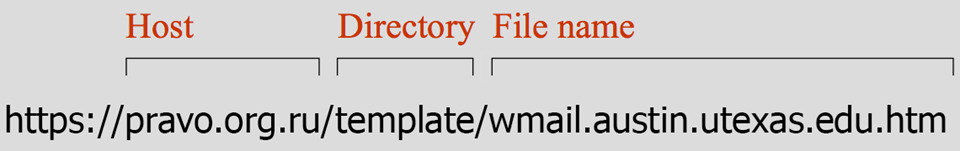
Websites are hosted on computers, much like the ones in your office. The Host part of a link tells you the name of the computer.
And just as your computer has files and folders on it, websites have them too. The Directory part of a link is just like a folder path on your computer. The very last piece of a link is the File name. It tells you the file you’re looking at, just like a Word document or spreadsheet on your computer.
So now we know what all this information means. What’s really important?
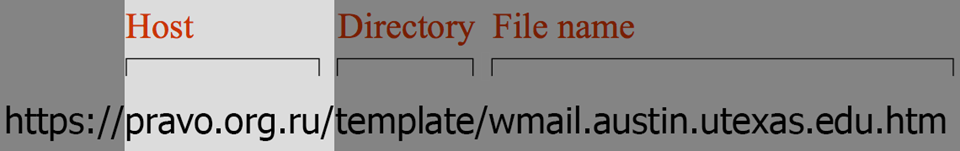
No matter how long and confusing a link is, the Host is all you need to focus on. Attackers can manipulate the Directory and File name to look like legitimate content, but they can never change their Host to perfectly match a legitimate one. Let’s look at a legitimate Host now.
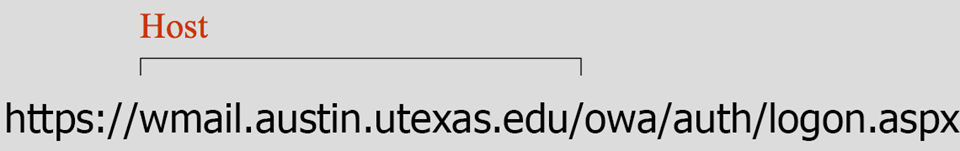
Now that we know the Host is what's really important, let's focus even more. Find the first single "/" in the link.
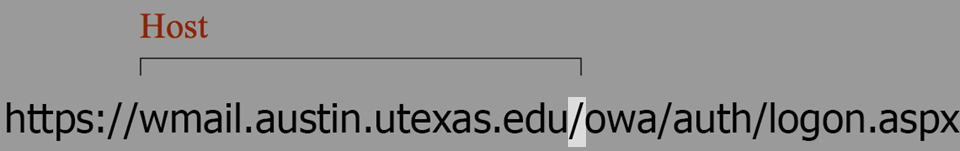
Look at the two words to the left of it, separated by a "." Those two words can never be manipulated; they always tell you a website’s true identity.
In the image below, those two words are "utexas" and "edu".
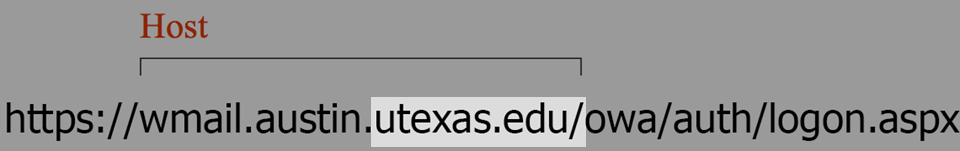

Compare the two images above. In the first, utexas.edu is the true source of the link, while the second one is org.ru. Look at the rest of the org.ru link. You can see its File name is trying to impersonate the Host of the first link!
Take a look at your web browser to find the address of the site you’re on, right now. What is its true source?
These clues should cast doubt on the legitimacy of the email and the associated webpage. Always check with your technical support contacts, the UT Service Desk, or the Information Security Office before clicking links in suspicious emails, or providing information to suspicious websites.
