You are seeing this page because you clicked a link in an email that wasn’t what it seemed.
Phishing emails entice you with attractive offers, or scare you with threats of loss, to trick you into visiting a malicious site and, often, handing over sensitive info. Had the email you received been an actual phish, clicking the link likely would have infected your computer or device with a "drive-by download". These malicious software programs are installed silently and attempt to steal your passwords, personal information, or even lock you out of your device.
If you suspect you've received a phishing email, forward it to postmaster@utexas.edu and notify your local IT staff.
Let’s learn how you can detect phishing attacks like these so you don’t get caught by a real attack.
Several clues should lead you to think twice about the legitimacy of this email: its sender address, its unsolicited nature, its content designed to pique your curiosity, its lack of any University business purpose, and its suspicious hyperlink. Let's look at the hard evidence:
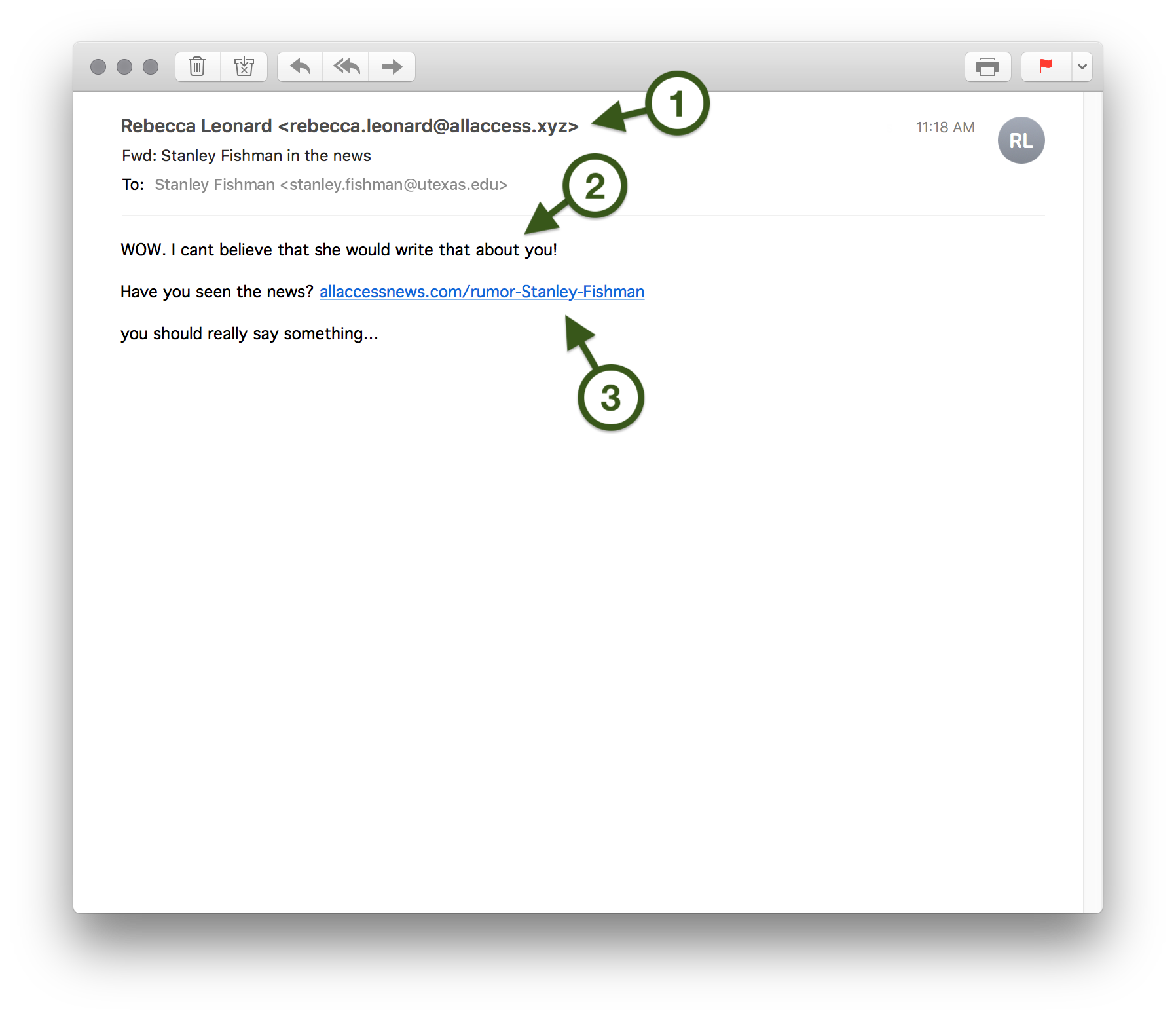
- Do you know a Rebecca Leonard? Chances are, you don't. But even if Rebecca is your best friend, check out her email address. It ends in allaccess.xyz, which is certainly not an official UT domain (like utexas.edu or austin.utexas.edu). This email came from an unknown and potentially unsafe sender.
- Subtle but noticeable grammatical errors (like the missing apostrophe in "can't") and missing capitalization at the beginning of the final sentence should raise doubts about this message. Most University communications are proofread and use standard grammar and English conventions.
- Sure, this link might have your name in it, but it appears to point to a website (allaccessnews.com) that is not operated by the University. Hovering over this link with your mouse before clicking it reveals that it points to an entirely different shady address—rumorpage.allaccess.xyz—which is definitely not part of the University’s official utexas.edu web presence. Need help inspecting hyperlinks in emails? Check out the Inspecting Links tab.
Apart from these specifics, consider the content of the message. It is clearly designed to pique your curiosity and get you to click—based on an unspecified rumor that an unknown stranger claims an unknown third party wrote about you. None of this sounds legitimate, and even less so when sent, unsolicited and out of the blue, to your official University address.
Several clues should lead you to think twice about the legitimacy of this email: its sender address, its unsolicited nature, its content designed to pique your curiosity, its lack of any University business purpose, and its suspicious hyperlink. Let's look at the hard evidence:
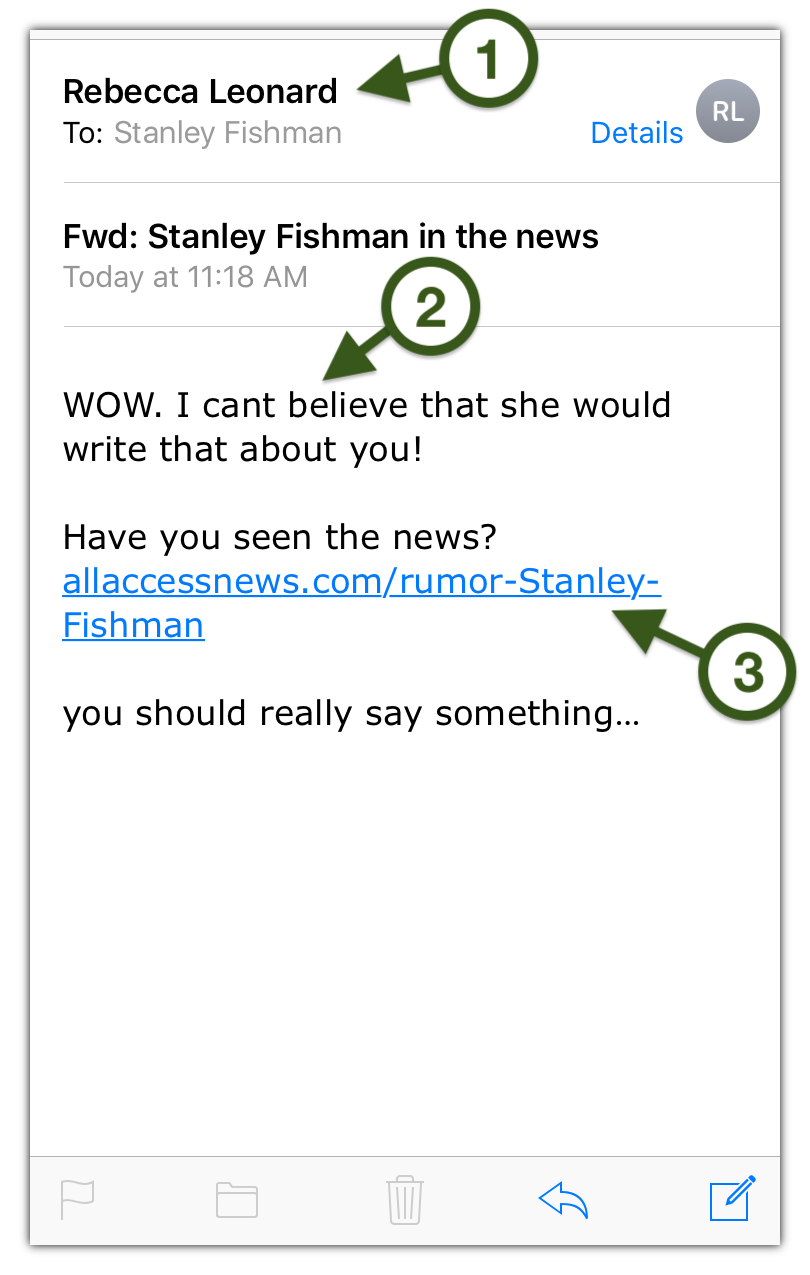
- Do you know a Rebecca Leonard? Chances are, you don't. But even if Rebecca is your best friend, check out her email address. It ends in allaccess.xyz, which is certainly not an official UT domain (like utexas.edu or austin.utexas.edu). This email came from an unknown and potentially unsafe sender. Note that, on mobile devices, you may need to tap on the sender's name or tap a "Details" button to see the sender's actual email address.
- Subtle but noticeable grammatical errors (like the missing apostrophe in "can't") and missing capitalization at the beginning of the final sentence should raise doubts about this message. Most University communications are proofread and use standard grammar and English conventions.
- Sure, this link might have your name in it, but it appears to point to a website (allaccessnews.com) that is not operated by the University. Long-pressing (tapping and holding for about one second) on this link before tapping it reveals that it points to an entirely different shady address—rumorpage.allaccess.xyz—which is definitely not part of the University’s official utexas.edu web presence. Need help inspecting hyperlinks in emails? Check out the Inspecting Links tab.
Apart from these specifics, consider the content of the message. It is clearly designed to pique your curiosity and get you to click—based on an unspecified rumor that an unknown stranger claims an unknown third party wrote about you. None of this sounds legitimate, and even less so when sent, unsolicited and out of the blue, to your official University address.
When you're inspecting a link, or on a website, how do you know it's legitimate or not?
Links have lots of information in them. They can be daunting. We'll break it down so you can focus on the most important part. Take this link, used in a real phishing attack.
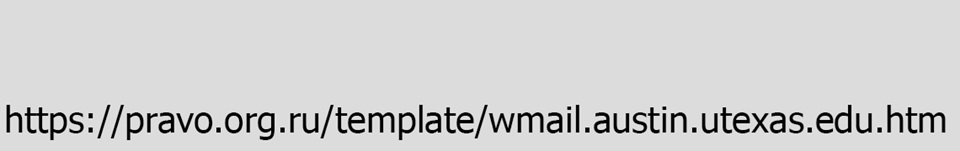
That's a lot of information, and some of it looks legitimate. But once you understand the structure of links, it becomes easy to see why this is a malicious link.
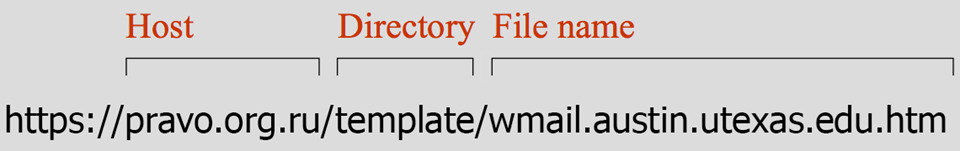
Websites are hosted on computers, much like the ones in your office. The Host part of a link tells you the name of the computer.
And just as your computer has files and folders on it, websites have them too. The Directory part of a link is just like a folder path on your computer. The very last piece of a link is the File name. It tells you the file you’re looking at, just like a Word document or spreadsheet on your computer.
So now we know what all this information means. What’s really important?
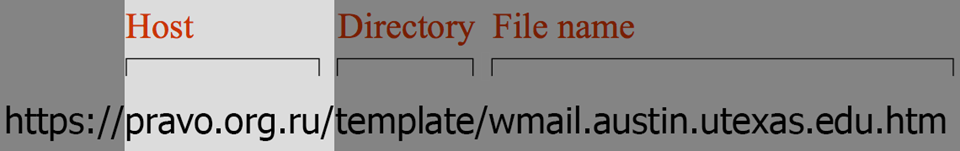
No matter how long and confusing a link is, the Host is all you need to focus on. Attackers can manipulate the Directory and File name to look like legitimate content, but they can never change their Host to perfectly match a legitimate one. Let’s look at a legitimate Host now.
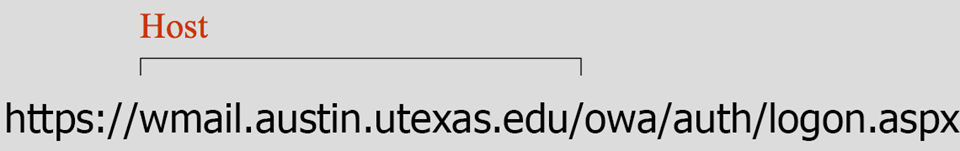
Now that we know the Host is what's really important, let's focus even more. Find the first single "/" in the link.
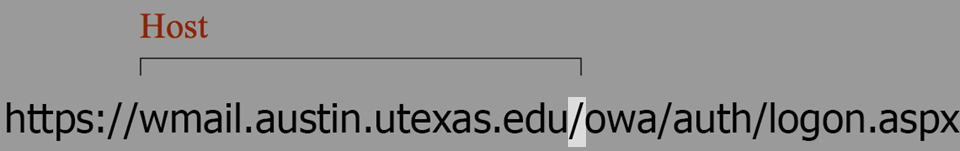
Look at the two words to the left of it, separated by a "." Those two words can never be manipulated; they always tell you a website’s true identity.
In the image below, those two words are "utexas" and "edu".
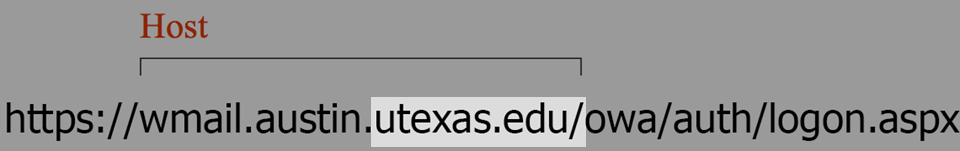

Compare the two images above. In the first, utexas.edu is the true source of the link, while the second one is org.ru. Look at the rest of the org.ru link. You can see its File name is trying to impersonate the Host of the first link!
Take a look at your web browser to find the address of the site you’re on, right now. What is its true source?
These clues should cast doubt on the legitimacy of the message. Always check with your technical support contacts, the UT Service Desk, or the Information Security Office before clicking links in suspicious emails, or providing information to suspicious websites.
