Table of Contents
Purpose
With Windows 10, Microsoft introduced some new features that 1) mine user data for the purpose of making the operating system more social and personalized, 2) collect data about user's habits and usage patterns for the purposes of diagnostics and troubleshooting, and 3) allow users to share Windows updates with local networks and the Internet in order to crowd-source distribution of updates. These features are enabled by default in all Windows 10 editions. The use of these new features pose a significant risk for exfiltration of confidential university data to Microsoft (and then to undisclosed third parties at Microsoft's whim), and, in the case of distributed updates, may violate state law governing the use of government property.
In order to comply with university policy, these features of Windows 10 must be disabled. This is best done through GPO for all domain joined machines, but instructions are also provided for stand-alone devices.
Scope
- All university-owned tablets, laptops, and desktops running Windows 10.
- All personally-owned tablets, laptops, and desktops running Windows 10 that are used to store confidential (Category I) university data.
Deployment Requirements
Professionally-Managed Devices
Use Group Policy or Local Policy as needed to make the following changes:
| Enforced1 | Policy Name | Policy Location | Applies To | Notes |
|---|---|---|---|---|
| Yes | Turn off Application Telemetry | Administrative Templates | Windows Components | Application Compatibility | At least Windows Server 2008 R2 or Windows 7 | Set to Enabled |
| Yes | Allow Telemetry | Administrative Templates | Windows Components | Data Collection and Preview Builds | At least Windows 10 Server, Windows 10 or Windows 10 RT | Set policy to Enabled and set Options to "0 - Off |LF||LF|Enterprise Only|RF||RF|" |
| Yes | Allow input personalization | Administrative Templates | Control Panel | Regional and Language Options | At least Windows Server Technical Preview 2, Windows 10 or Windows RT 8.1 | Set to Disabled. This disables the use of Cortana, collection of speech and handwriting patterns, typing history, contacts, and calendar information. |
| Yes | Allow Cortana | Administrative Templates | Windows Components | Search | At least Windows Server Technical Preview 2, Windows 10 or Windows RT 8.1 | Set to Disabled |
| Yes | Turn off picture password sign-in | Administrative Templates | System | Logon | At least Windows Server 2012, Windows 8 or Windows RT | Set to Enabled |
| Yes | Accounts: Block Microsoft Accounts | Windows Settings | Security Settings | Local Policies | Security Options | At least Windows Server 2012, Windows 8 or Windows RT | Check "Define this policy setting" and choose "Users can't add or log on with Microsoft Accounts" |
| No | Turn off the Advertising ID | Administrative Templates | System | User Profiles | At least Windows Server 2012 R2, Windows 8.1 or Windows RT 8.1 | Set to Enabled. This is not required, but is recommended to protect user privacy. |
| No | Use Microsoft Passport for Work | Administrative Templates | Windows Components | Microsoft Passport for Work | At least Windows 10 Server or Windows 10 | Set as desired. This functionality is used with biometrics and PINs |
| No | Turn on PIN sign-in | Administrative Templates | System | Logon | At least Windows Server 2012, Windows 8 or Windows RT | Set as desired. If PINs are allowed, they must comply with section 15.2 of the Information Resources Use and Security Policy. |
| Yes | Use digits Use lowercase letters Maximum PIN Length Minimum PIN Length Use special characters Use uppercase letters | Administrative Templates | Windows Components | Microsoft Passport for Work| PIN complexity | At least Windows 10 Server or Windows 10 | All passwords, including device PINs, must comply with section 15.2 of the Information Resources Use and Security Policy. Another option is to disable PIN sign-in entirely. |
| Yes | DownloadMode | Preferences | Windows Settings | Registry | All versions of Windows will accept the registry change, but will only be effective on Windows 10 | This registry policy preference will disable peer-to-peer update sharing and should be created with the name "DownloadMode" as a "Replace" action, in the HKEY_LOCAL_MACHINE hive, at the "SOFTWARE\Microsoft\Windows\CurrentVersion\DeliveryOptimization\Config" key. The value type is "REG_DWORD", and the value data is "0". On the Common tab, the setting "Remove this item when it is no longer applied" should be checked. |
1 These requirements will be enforced by GPO for all members of the Austin Active Directory domain.
This guide assumes that the operating system is already installed. All of these settings may also be configured during installation if "Customise settings" is chosen during the "Get going fast" stage of installation.
Follow the instructions to make the following changes:

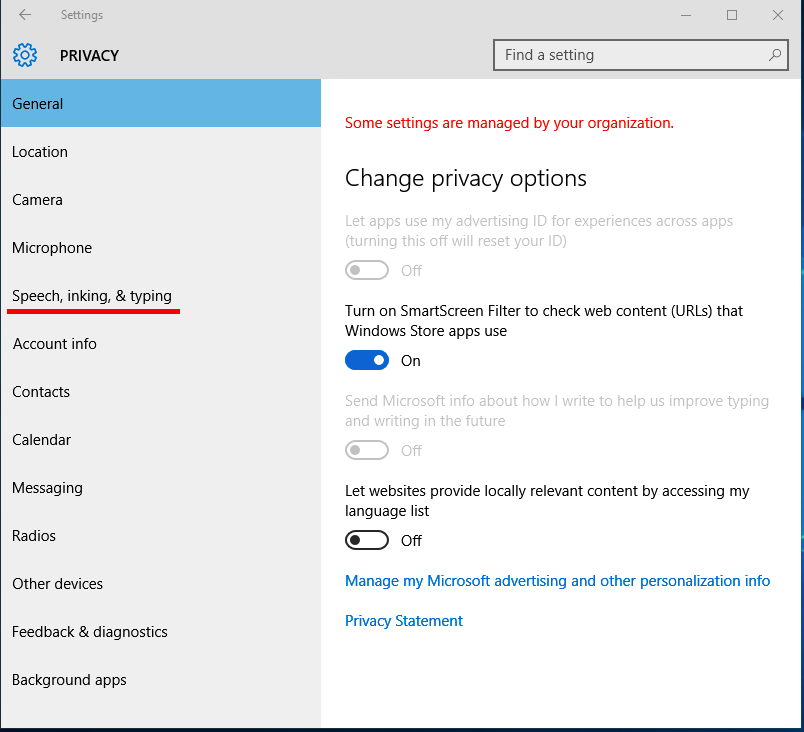


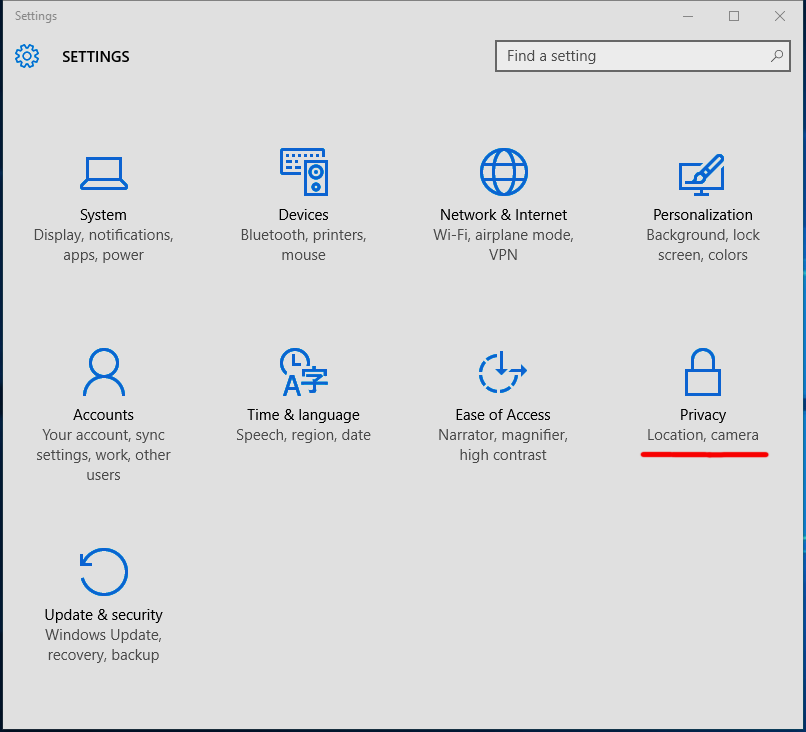
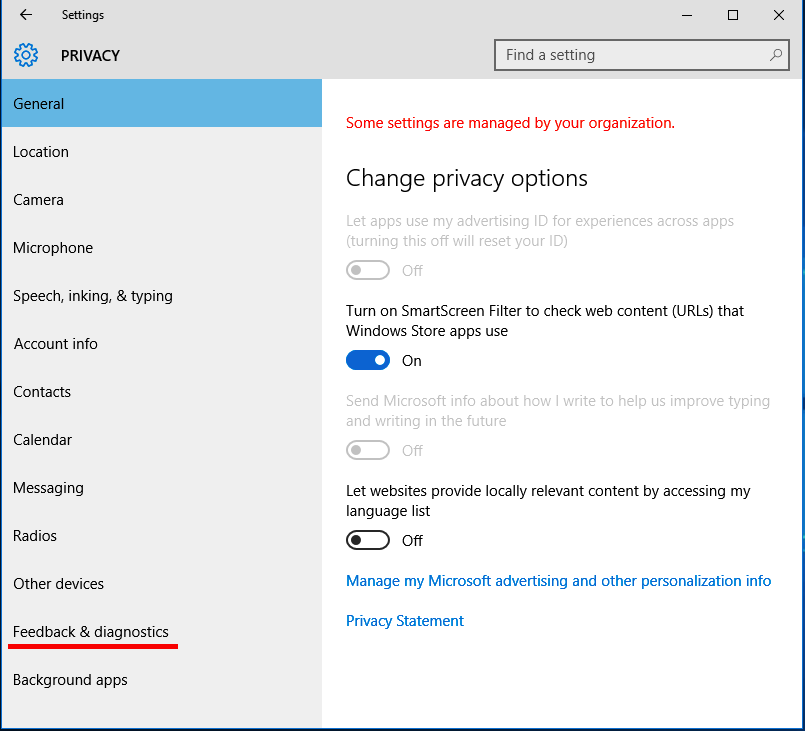

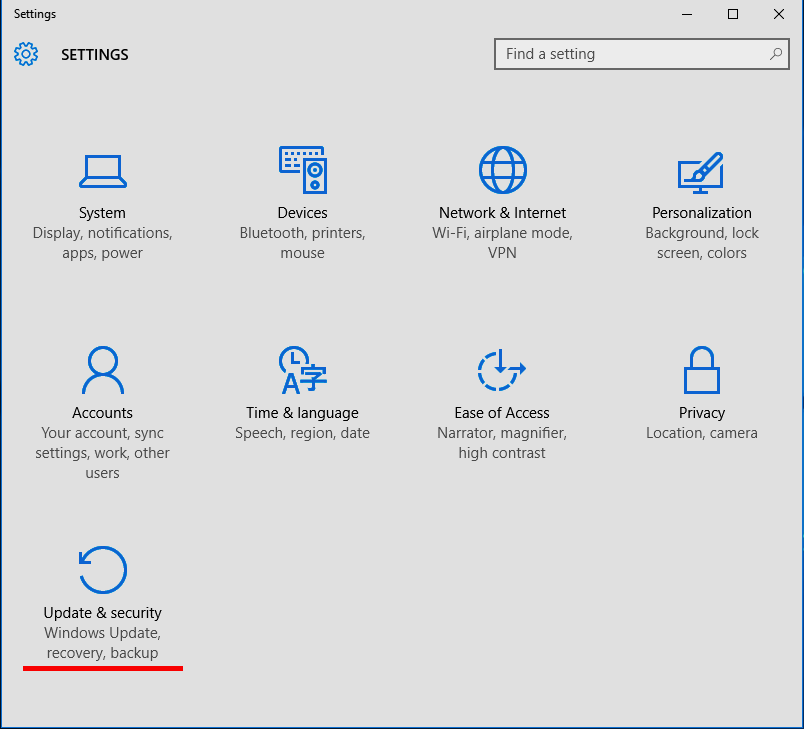






Non-Compliance and Exceptions
If any of the configuration requirements contained within this document cannot be met, an Exception Process must be initiated that includes reporting the non-compliance to the Information Security Office, along with a plan for risk assessment and management. (See Security Exception Report.) Non-compliance with these standards may result in revocation of system or network access, notification of supervisors, and reporting to the Office of Internal Audit.
University of Texas at Austin employees are required to comply with both institutional rules and regulations and applicable UT System rules and regulations. In addition to university and System rules and regulations, University of Texas at Austin employees are required to comply with state laws and regulations.
The policies and practices listed here inform the system hardening procedures described in this document and with which you should be familiar. (This is not an all-inclusive list of policies and procedures that affect information technology resources.)
Information Resources Use and Security Policy (IRUSP)
UT Austin Acceptable Use Policy (AUP)
UT Austin Minimum Security Standards for Systems
External References
Optional Privacy and Security Settings for all Windows 10 Devices
Privacy-conscious users may find the guides below useful for addressing other features of Windows 10 that pose a privacy/security risk:
- http://www.howtogeek.com/221864/digging-into-and-understanding-windows-10s-privacy-settings/
- https://fix10.isleaked.com/ - this site is currently unavailable, but a cached copy of the page is at: https://web.archive.org/web/20150908131637/https://fix10.isleaked.com/
