A number of departments on campus have started to use ATA password security in combination with Full Disk Encryption (FDE) drives, or Self-Encrypting Drives (SED), to comply with the mandatory encryption policy for portable devices without having to install encryption applications such as SecureDoc. There are number of benefits to this approach:
- Performance of the computer is unaffected as the encryption is done by the drive controller and not at the operating system level.
- Encryption is always on and cannot be disabled.
- All operating systems and platforms are supported. It functions identically to a non-encrypted drive after authentication.
- Multi-boot environments are supported.
With an SED, data written to the drive is always encrypted using a manufacturer-set encryption key. This key can only be changed using specialized (but available) tools, and doing so destroys any existing data. In its default mode of operation though, an SED will decrypt any data upon request, functioning identically to a non-SED drive. This is perhaps better explained from Seagate’s FAQ:
How do I setup an FDE drive?
Every Seagate FDE drive is built to encrypt all data, all of the time, right out of the box. Each drive has a unique encryption key, which results in every drive, given the same data to write, saving uniquely different data patterns to the media. This encryption process is transparent to the user and to the operating system. Therefore, an FDE drive without any passwords controllingaccess, behaves like a non-FDE drive. It is the activation of passwords through either ATA Security or the richer Seagate Secure feature set that protects the drive from unauthorized access.
A new FDE drive loads the operating system and any other applications just like a non-FDE drive. Third-party FDE drive management software which implements the Seagate Secure password controls is loaded after the initial OS and applications are setup. In lieu of third-party software, traditional ATA Security passwords can be used to protect the drive from unauthorized access.
So, setting an ATA password on a drive is one option to prevent users from reading and writing to the drive until they authenticate. This security is part of the ATA standard and has existed for some time. Different vendors implement the standard slightly differently. For example, when users are prompted to enter the password during boot-up and the exact characteristics a password may have (e.g. password length and support for special characters) will vary between manufacturers. Some computers, most likely desktops, may not even have the option to enable an ATA password. ATA passwords also prevent swapping drives from one computer to another unless you know the password - access to the data on a different computer is still restricted. Using an SED with an ATA password adds protection against physical platter observation, since the data is always encrypted at rest.
It's very important to understand that even though data on an SED is always encrypted, since the drive controller will decrypt data upon request, some mechanism to restrict access from unauthenticated users must be implemented. While the use of ATA password security to accomplish this authentication is an approved encryption method for laptops, there are several risks to be aware of before deciding to go this route. ATA password security can be broken in a number of ways:
- While read/write operations to the drive are restricted, firmware updates are not. Hacked firmwares may be available that can remove or disable the ATA passwords.
- Hardware devices and software applications are readily available that can break the password through brute force, vendor back door passwords, and other techniques.
- Data recovery services can obtain a copy of the unencrypted data through direct platter observation. This method only applies to non-FDE disks. However, a number of these same services also advertise removal of unknown passwords and this would present a risk to FDE drives as well.
- Calling the manufacturer. Dell, for example, has a utility that uses the service tag of a computer to generate a master password, which can override an unknown password and provide access to the data. Dell also provides a configuration option (Security Erase) that will destroy all data on the drive if this master password is ever used, but implementation of such a feature by other manufacturers will vary.
To demonstrate how trivially this protection can be bypassed, the ISO evaluated the application A-FF Repair Station, which advertises the ability to remove unknown ATA passwords from a wide selection of drives. This application does not yet support Seagate's portable line of drives, perhaps the most commonly used SEDs on campus, so for our evaluation we used a Western Digital desktop drive. The software additionally requires that the drive to be unlocked be connected over SATA (or ESATA) and that it not be the boot drive, so we used a Dell Precision T7400 which can handle multiple internal drives and also has the BIOS option to configure ATA passwords (not all desktops do). After getting this all set up, actually removing an unknown ATA password required only five simple steps:
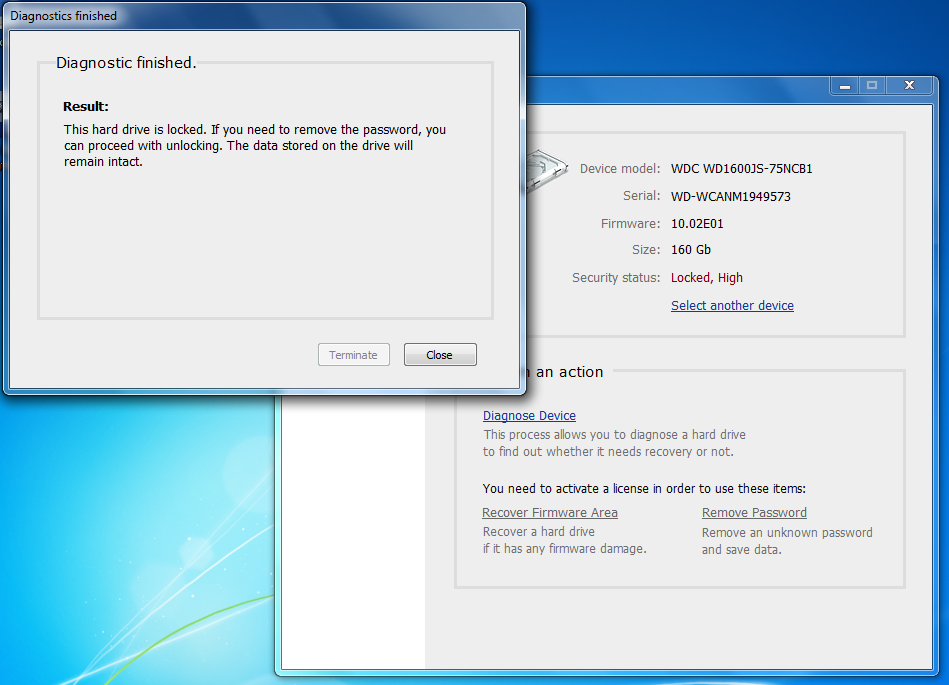
Run a diagnostic on the desired drive to verify that it is supported. The diagnostic routine is free; other operations will require a valid license.
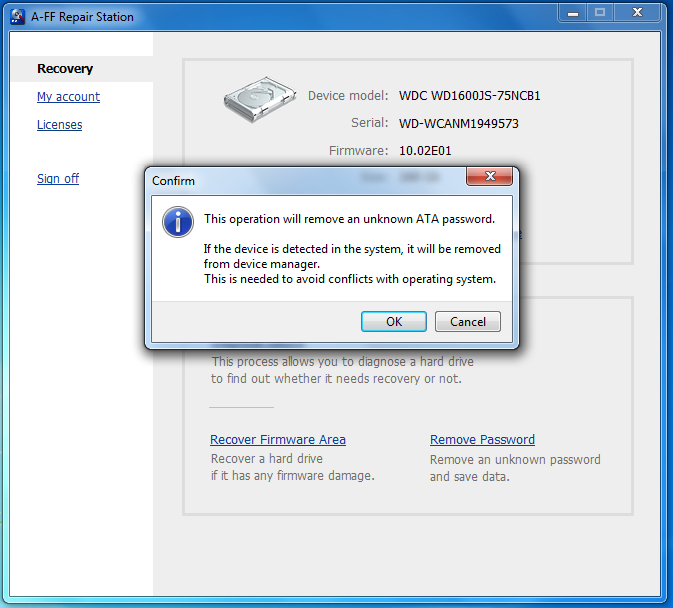
Select Remove Password from the list of options after you have verified that your drive is supported (via the diagnostic) and purchased a license.
Click Okay to begin the removal process.
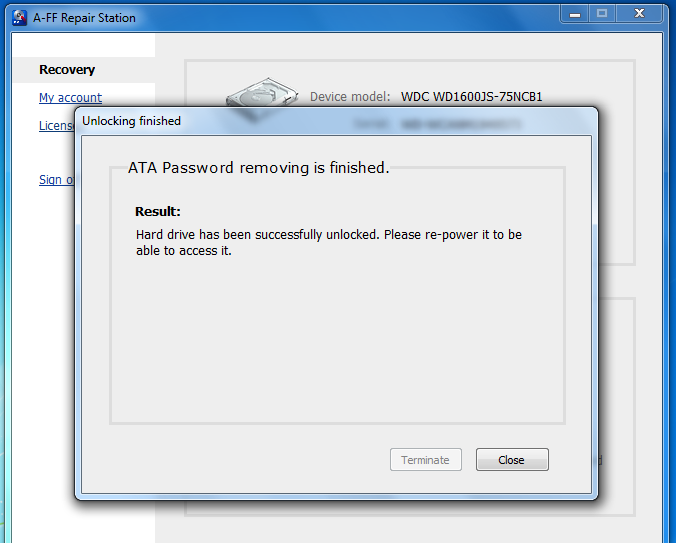
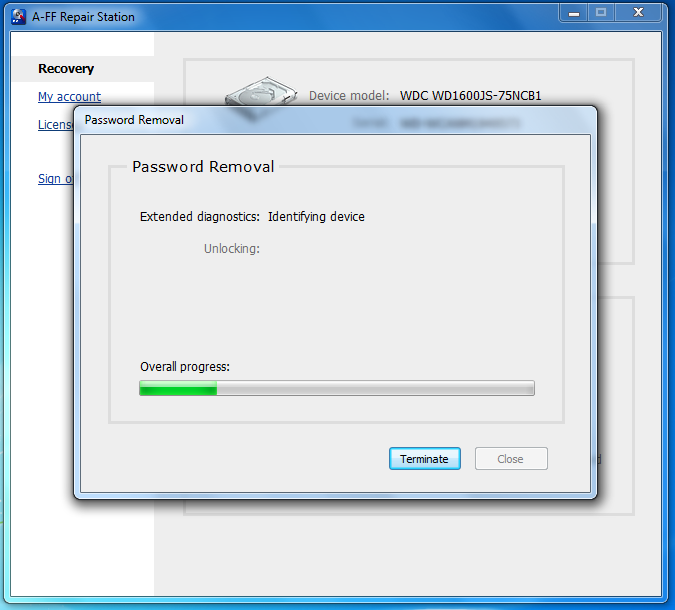
If all goes well, the password will be removed in a few seconds.
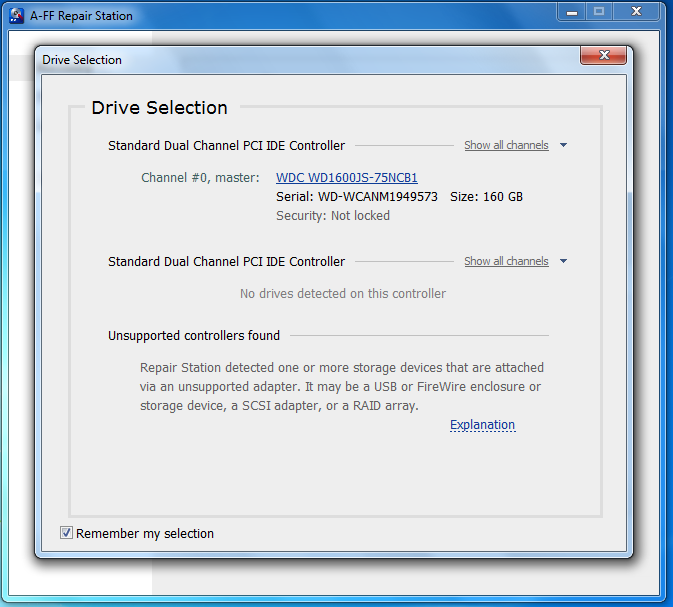
After restarting, you can see the drive no longer has a password set. This operation is non-destructive to the data! All data that was present on the drive is now accessible.
Ultimately, given the ease with which ATA password security can be defeated the Information Security Office strongly recommends against this approach. SEDs are very compelling options for dealing with encryption requirements. However, the most secure way to utilize SEDs is to have a third party management application like WinMagic's SecureDoc, Wave's Embassy Security Center, or Secude's FinallySecure Enterprise. These enterprise applications can interface with SEDs using the manufacturer provided APIs (e.g. Seagate Secure for Seagate drives) to securely handle user authentication, while still relying upon the SED hardware itself to handle the encryption. With this you maintain all of the benefits of SEDs and also gain the ability to have passwords escrowed automatically, demonstrate that a device was encrypted in the event it was lost or stolen, and remotely erase devices.
